IndexExchangecom: Ad Tech Platform Guide
페이지 정보

본문
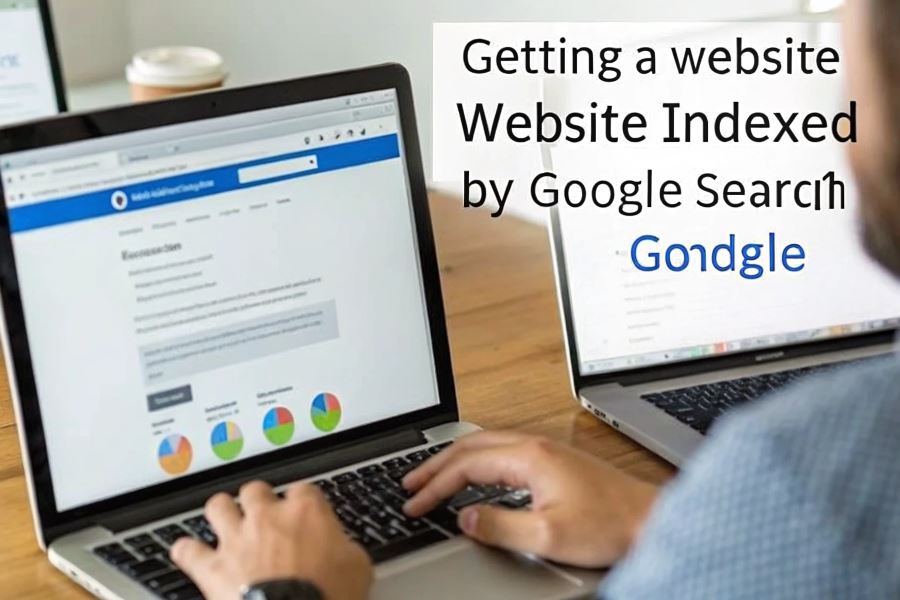
IndexExchangecom: Ad Tech Platform Guide
Who can benefit from SpeedyIndexBot service?
The service is useful for website owners and SEO-specialists who want to increase their visibility in Google and Yandex,
improve site positions and increase organic traffic.
SpeedyIndex helps to index backlinks, new pages and updates on the site faster.
How it works.
Choose the type of task, indexing or index checker. Send the task to the bot .txt file or message up to 20 links.
Get a detailed report.Our benefits
-Give 100 links for indexing and 50 links for index checking
-Send detailed reports!
-Pay referral 15%
-Refill by cards, cryptocurrency, PayPal
-API
We return 70% of unindexed links back to your balance when you order indexing in Yandex and Google.
→ Link to Telegram bot
Imagine searching for a crucial file within a vast, complex file system. The speed and efficiency of that search depend heavily on how your operating system and file system handle symbolic links. This is where understanding how options indexes interact with symlinks becomes critical.
Different file systems, such as ext4 and btrfs, employ varying strategies when encountering symbolic links during indexing. The way these indexes process symlinks directly impacts the performance of file searches and overall system resource consumption. For instance, some indexes might follow symlinks during the indexing process, effectively incorporating the target file’s metadata into the index. This approach, where the index follows the symbolic link to the actual file, can lead to a more comprehensive search but might also increase indexing time and resource usage.
Ext4 vs. Btrfs: A Comparative Look
Let’s consider the behavior of two popular file systems: ext4 and btrfs. Ext4, a widely used file system, generally handles symlinks efficiently, but its indexing strategy might not always follow every symlink. Btrfs, on the other hand, offers more advanced features and might employ a more comprehensive approach to symlink handling during indexing, potentially impacting performance differently. The exact behavior can depend on the specific configuration and version of each file system.
Performance Implications: Speed and Resource Usage
The performance implications of symlink traversal during indexing are significant. Following symlinks can lead to increased indexing time, especially in file systems with a large number of symbolic links. This increased processing time translates to slower search speeds. Furthermore, the process can consume more system resources, such as CPU cycles and memory, potentially impacting the overall system responsiveness. Understanding these trade-offs is crucial for optimizing file system performance and ensuring efficient data retrieval.
Taming Symlinks: Index Configuration Strategies
Managing symbolic links within your file system indexing can be a surprisingly complex task. The seemingly simple act of indexing files can quickly become a minefield when dealing with symlinks, potentially leading to inaccurate search results, bloated indexes, and even security vulnerabilities. Understanding how your chosen file system handles these links—whether it follows them or ignores them—is crucial. options indexes followsymlinks, for example, is a critical consideration when setting up your indexing strategy. This often-overlooked aspect can significantly impact the efficiency and accuracy of your search functionality.
File System Variations
Different file systems offer varying levels of control over symlink handling. Some, like ext4 (commonly used in Linux), provide granular options for configuring how the indexing service interacts with symbolic links. Others might offer less flexibility, requiring workarounds or alternative indexing solutions. For instance, you might need to explicitly tell your indexing service to not follow symlinks pointing to directories to avoid indexing the entire contents of potentially massive subtrees. This is especially important when dealing with large datasets or shared network drives.
Command-Line Control
The command-line interface provides the most direct way to manipulate indexing settings related to symbolic links. Tools like updatedb (often used with locate), which updates the system’s locate database, allow you to specify options to control symlink behavior. For example, you can use flags to prevent updatedb from following symlinks, thus ensuring only the symlink itself, not its target, is indexed. This is particularly useful for managing temporary or dynamically generated links. Understanding the specific flags and options available for your indexing tools is paramount.
| Tool | Option for No-Follow | Option for Follow | Notes |
|---|---|---|---|
updatedb | -S or --prune-symlinks | (No explicit option) | Requires careful consideration of the implications for your workflow. |
mlocate | -f | (No explicit option) | Similar to updatedb, careful planning is necessary. |
Remember that the exact commands and options might vary depending on your operating system and the specific indexing tools you’re using. Always consult the documentation for your chosen tools to ensure you’re using the correct syntax and options.
Practical Examples and Best Practices
Let’s consider a practical scenario. Imagine you have a large project directory with many symbolic links pointing to different versions of source code. If your indexing service follows these symlinks, your index will become bloated with redundant entries, slowing down searches and consuming unnecessary disk space. By configuring your index to not follow symlinks in this case, you ensure that only the main project directory and the symlinks themselves are indexed, resulting in a more efficient and accurate search experience.
Conversely, if you have a specific need to index the contents of a directory accessed via a symlink, you would configure your indexing service to follow the link. This requires careful consideration of the potential impact on index size and search performance. Always weigh the benefits of indexing the target against the potential drawbacks of a larger, slower index.
Choosing the right strategy requires a deep understanding of your data structure and your indexing needs. Careful planning and testing are essential to ensure that your indexing strategy aligns with your specific requirements and avoids potential pitfalls. Regularly reviewing and adjusting your configuration as your data evolves is also a best practice.
Navigating Symlink Risks in Indexed Files
Imagine this: your carefully curated options index, a vital component of your application’s file management, unexpectedly leads to unintended locations. This isn’t a bug; it’s a potential security vulnerability. When options indexes follow symbolic links, they open a door to malicious activity if not properly managed. The seemingly innocuous act of allowing your index to traverse symlinks can have significant repercussions. Let’s explore how.
The core issue lies in the nature of symbolic links themselves. A symlink, essentially a pointer to another file or directory, can be manipulated. If an attacker can create a symlink pointing to a sensitive location—perhaps a database file or a configuration file—and your options indexes follow symlinks, they gain access to data they shouldn’t. This is a classic symlink attack. The index, designed to organize and access files, becomes a conduit for unauthorized access. This is especially critical in environments where user-supplied data is involved, as it could allow attackers to read, modify, or delete sensitive information.
Mitigating Symlink Dangers
The good news is that these risks are mitigable. The first line of defense is careful control over the creation and modification of symbolic links. Implement strict access control lists (ACLs) to limit who can create symlinks within your system. Regular security audits, including checks for suspiciously placed symlinks, are crucial. Automated tools can assist in this process, flagging unusual link activity.
Data Integrity Safeguards
Beyond access control, ensuring data integrity requires a multi-pronged approach. Regular backups are paramount. In the event of a successful symlink attack, having a clean backup allows for swift recovery. Consider using checksums or cryptographic hashes to verify the integrity of your files. Any discrepancy between the expected and calculated hash indicates potential tampering. This method provides an extra layer of protection against subtle modifications that might go unnoticed otherwise.
Advanced Techniques
For more robust protection, explore advanced techniques like chroot jails or containers. These technologies isolate processes, limiting their access to the file system. Even if a symlink attack is successful, the damage is contained within the isolated environment. Consider using tools like Docker https://www.docker.com/ or similar containerization technologies to enhance your security posture. Remember, a layered security approach is the most effective.
A Proactive Stance
Ultimately, preventing symlink-related security breaches requires a proactive approach. Regular security assessments, robust access controls, and the implementation of data integrity checks are not just best practices; they are essential safeguards in today’s threat landscape. By understanding the potential risks and employing the appropriate mitigation strategies, you can significantly reduce the likelihood of successful attacks and maintain the integrity of your valuable data.
Telegraph:Google Index WordPress Site|SEO Guide 2025
- 이전글IndexGuru: SEO Optimization & Best Practices 25.06.13
- 다음글Multi-Key Indexes: Boost Database Performance 25.06.13
댓글목록
등록된 댓글이 없습니다.
